Notes, tutorials and walkthroughs on infosec, programming and Linux related topics.
Saturday, February 15, 2014
Tool of the day - Netstat
Netstat is a very important tool for gathering information about the connections on a machine or troubleshooting network problems. It's a default utility for both Windows and Linux, thus there is no excuse in not getting familiar with it, it's very useful for any system admin, network guy or good old home user that would like to know what really is coming and going to and from his computer.
If ran with no arguments, netstat produses an overwhelming output of all the open sockets in the system. Something like this (note that the output was piped to less and I only show the first page for brevity
A cleaner way to zoom on the information that might be of interest is to use the -p argument to display the PID and the name of the program to which each socket belongs, along with the path.
If we're only interested in the listening sockets, we can use the -l option
And the most comprehensive option is -a, short for all, which combines all the information, showing the listening sockets and the established connections.
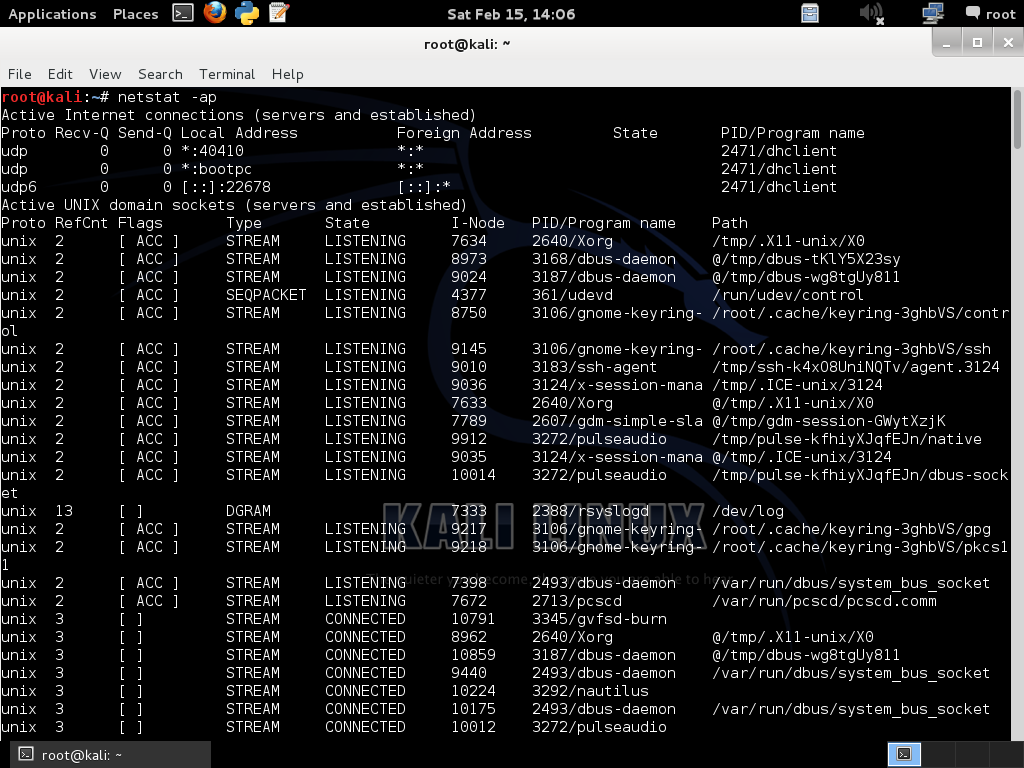
Combining options can yield the desired amount of information when we are searching for something specific. For instance, we could combine the -a and -p arguments like this: nestat -ap. Now we can also see which program is associated with all the connections and listening sockets
If we're interested only in the TCP connections:
We can see here a connection to an FTP server
Or if we want to see the TCP connections and the programs associated with them:
Note the -n option, which is used to display the numeric value for addresses and ports, instead of resolving them to their names (IP address instead of host names and port numbers instead of names). An example is that we're seeing port 80 instead of http. We can see there's an FTP server running, among other things.
Netstat can be very handy in a variety of scenarios. If we wanted to harden a server, we could go through netstat output and see what's listening, and if we really need that program. Or, we could discover suspicious connections in the case of a compromised machine. If nothing else, we could impress the less tech savvy persons around us with the dark magic of the command line and mysterious output on the screen that makes sense to us. It pays to get familiar with this utility, since there will certainly be occasions to use it.
Subscribe to:
Post Comments (Atom)






No comments:
Post a Comment